Two-factor authentication (2FA) is multi-factor authentication (MFA). Both authentication solutions provide additional account security by requiring additional factors of authentication. To understand how exactly 2FA and MFA differ, it’s firstly important to understand the concepts of authentication and factors of authentication.
What is Authentication?
Authentication is a fundamental concept of identity access management (IAM) that enables a system to verify the identity of a user. Factors of authentication are security mechanisms that prove a user is who they claim to be before granting access. There are three types of authentication factors, including:
- Knowledge factor (something you know): e.g., a one-time password (OTP), a personal identification number (PIN)/passcode, an answer to a security question
- Possession factor (Something you have): e.g., a mobile device or another physical device, a fob, a hardware token (e.g., Yubikey), a security token/ security key
- Inference factor (Something you are): e.g., biometrics, such as fingerprints, facial recognition, retina scan, voice recognition
Two-Factor Authentication vs. Multi-Factor Authentication
The definitions of two-factor and multi-factor authentication, and the differences between these security mechanisms, are listed below.
What is Two-Factor Authentication (2FA)?
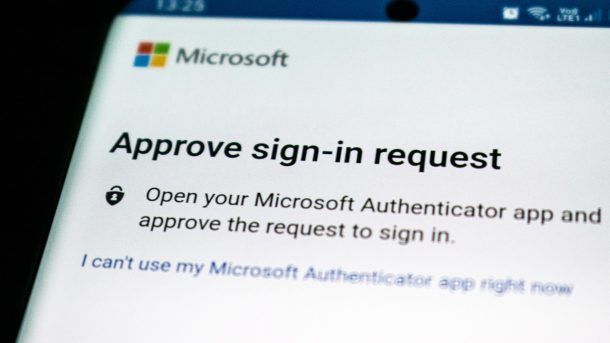
Two-factor authentication (2FA) is a type of multi-factor authentication (MFA) that verifies end users’ identities based on two factors before granting access to online accounts.
Below is an example of 2FA in action:
A user attempts to log in to an online service with their username and password.
The system confirms the login credentials are correct, prompting the second authentication factor.
The user receives a push notification (possession factor) to confirm they are attempting to log in.
The user is redirected to the service’s login page and prompted to use facial recognition (biometric factor).
The system verifies the facial recognition attempt and grants access to the user.
2FA vs. MFA
Below is a summary of the difference between 2FA and MFA:
2FA is a subset of MFA
All instances of 2FA are instances of MFA.
Not all instances of MFA are 2FA.
MFA requires more pieces of evidence than 2FA to grant users access
Why are 2FA and MFA Important?
Most financial, healthcare, educational, and government institutions now facilitate online accounts. These service providers store personally identifiable information (PII), protected healthcare information (PHI), and other confidential information. Account protection once relied on single-factor authentication (SFA) methods – usually the use of passwords. These are no longer enough on their own.
Cybercriminals in today’s threat landscape are highly specialized in gaining unauthorized access to sensitive data, especially via SFA logins. There are many techniques hackers can use to steal passwords and exploit users’ personal information for malicious purposes.
Standard password-stealing methods include:
Brute-force attacks: In this type of cyber attack, a hacker strategically guesses a user’s password until they crack the correct combination. This method has an exceptionally high success rate when users have weak passwords, e.g., birthdates.
Data leaks: A user/service accidentally expose sensitive data on the Internet, which a hacker finds and exploits to gain unauthorized access, e.g., a birthdate on LinkedIn. Leaked credentials from historical data breaches provide hackers an even easier attack vector. Despite its major security issues, many people still reuse the same passwords across different accounts. Attackers can use these compromised passwords across multiple accounts for the same user until they find a successful login combination.
Keyloggers: Hackers install this type of malware on unsuspecting users’ systems. Keyloggers record keystrokes and read clipboard data on hacked devices, allowing hackers to steal passwords and other information which could allow unauthorized access.
2FA and MFA prevent cybercriminals from taking advantage of compromised passwords by relying on additional authentication methods. Unlike SFA, if a hacker steals a user’s password, they still can’t gain access to the user’s account. They’ll still have to provide at least one additional authentication – inherence or biometric – something they are less likely capable of doing.
Is MFA More Secure Than 2FA?
Both 2FA and MFA are much more secure forms of authentication than single-factor authentication (SFA), relying on more than just a password. MFA is usually considered safer than 2FA as it provides the most layers of security against cyber criminals. However, the strength of an MFA solution depends on how secure its additional authentication methods are.
For example, the possession factor of email and SMS verification codes is not as secure as other types of authentication. The abundance of phishing scams across both platforms and the ability to hack SIM cards create additional cybersecurity risks. MFA is most effective when it relies upon biometric authentication factors, which are unique to the user and difficult to replicate.